What is an Intrusion Detection System (IDS)?
IDS is a system that monitors traffic for suspicious activities. It issues alerts on detecting suspicious system behavior. Any malicious program or lines of code get reported to the admin using an existing set of data. Although IDS triggers alert for suspicious activities, it often gets exposed to false threats. It is the reason why an IT firm needs to fine-tune IDS when it installs the software.
How Does An IDS System Differ From IPS?
An intrusion detection system assesses network traffic and inspects signs of possible cyber-attacks. Intrusion prevention systems (aka IPS) inspect encrypted data packets. It can stop data packets from getting delivered based on the nature of network traffic.
The main difference between IPS and IDS is that the former is a control system. IDS is a system used for monitoring data traffic. IDS compares network activity to an existing threat database. IDS takes help from an individual to look at the data traffic.
[Read more: What is Content://com.avast.android.mobilesecurity/temporarynotifications?]
What Are The Types Of IDS Systems?
- NIDS (aka network detection system) gets installed at checkpoints. NIDS monitors data traffic from all devices localized on the network.
- HIDS (aka host detection system) gets installed on multiple hosts or servers across the network. HIDS detects traffic from the specific device and alerts the system admin to detect suspicious activities.
- APIDS (aka protocol-based detection system) is an agent that resides on a pool of servers. It monitors data traffic by interpreting communication on app-based protocols.
- CIDS (aka Hybrid detection system) is the resultant combination of one or more IDS systems. It needs system admins to configure host agents with network protocols to get a complete view of the system.
Intrusion Detection Systems (IDS) Vs. Intrusion Prevention Systems (IPS)
| Sr.No. | Intrusion Detection System | Intrusion Prevention System |
| 1. | Intrusion detection systems are monitoring and detection tools. | An intrusion prevention system is a prevention control system. |
| 2. | The tools of the Intrusion Detection System don’t take action on their own. | The control system of IPS accepts and rejects the packets based on a certain ruleset. |
| 3. | An intrusion detection system requires human intervention or another system to look at the results. | Intrusion prevention system requires regular updating of the new possible data threats. |
| 4. | An intrusion detection system is not inline so traffic doesn’t require to flow through it. | The intrusion Prevention System is in line where traffic needs to flow through it. |
| 5. | There are two types of IDS: Network Intrusion Detection System (NIDS) and Host-based IDS (HIDS). | There are 4 types of IPS: Network-based IPS (NIPS), Wireless IPS (WIPS), Host-based IPS (HIPS), and Behavior IPS. |
How to Choose the Best Intrusion Detection System?
There is numerous intrusion detection system available in the market but to choose the best among all the available system requires a lot of research. Here we have explained various factors you need to keep in mind while choosing the best intrusion detection system. These are mentioned as follows:
- First, try to research out your business needs and systems that are available.
- Is the IDS system going to support the current network?
- Consider the budget for both IDS/IPS systems.
- Wireless/Wired network support
- What happens If something goes wrong with the current system
- Whether the system can be scaled to bigger with the existing system
- Interoperability
- Timely updates to new or modified signature for prevention/detection of threats.
[Read more: Is LDPlayer Safe and Free to Use?]
List of the Best Intrusion Detection Software
Here is the top 10 list of best intrusion detection software explained in a detailed manner as follows:
1. SolarWinds Security Event Manager
SolarWinds Security Event Manager is an IDS that runs on a windows server platform. It is best for clients who are having large businesses.
Features:
- Real-Time Monitoring
- Compliance Tracking
- Data Visualization
- User Activity Monitoring
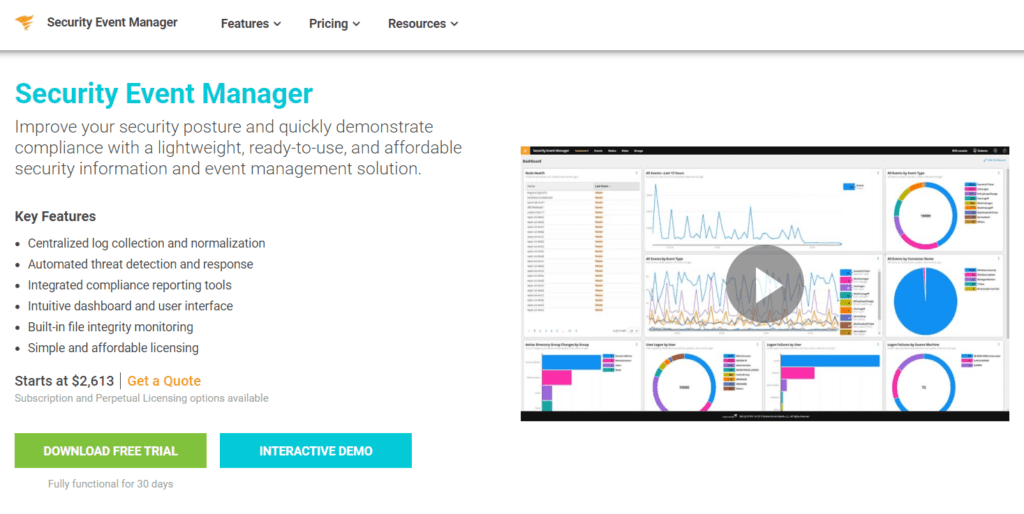
Website: https://www.solarwinds.com/security-event-manager
Pricing: Pricing starts from $2613 as a one-time payment with 30 days free trial.
2. Zeek
Zeek is also known as Bro which is a network-based intrusion detection system (NIDS) that operates on live traffic data. This tool can be installed freely on UNIX, Linux, and Macintosh OS platforms.
Features:
- Open Source with a BSD License
- Analysis of Real-Time Data
- Standard Interface
- IPv6 Support
Website: https://zeek.org/
Pricing: Zeek is open-source which is available free to use.
[Read more: What is content://com.android.browser.home/?]
3. OSSEC
OSSEC is an open-source Host-based Intrusion detection system that is free for usage. It can be run on UNIX, Windows, Macintosh OS, and Linux platforms but doesn’t have a user interface.
Features:
- It is open source
- Log Based IDS
- Active Response
- Malware and Rootkit Detection
Website: https://www.ossec.net/
Pricing: As it is open-source it is free to use.
4. Fail2Ban
Fail2Ban is a lightweight and free Intrusion prevention system that runs on the command line interface and is available on UNIX, Macintosh OS, and Linux platforms.
Features:
- Log File Analysis
- Open Source
- Automatic blocking of suspicious IP addresses
- Compatible with Unix and Macintosh OS Systems
Website: http://www.fail2ban.org/wiki/index.php/Main_Page
Pricing: It is open-source that is free to use.
5. Snort
Snort is a well-known Network-based Intrusion Detection/Prevention System that has a huge community of users. It is widely accepted as many other available Intrusion detections and Prevention systems are built to be compatible with it.
Features:
- Open Source
- Cross platform which runs on all operating systems.
- Huge library of prebuilt detection rules.
- Rules can be easily implemented.
Website: https://www.snort.org/
Pricing: Snort is free to use but the rule subscriptions start from $29.99 for personal use to $399 for business use annually for both of them.
6. Kismet
Kismet is a wireless network detector, packet sniffer, and IDS which is different from other wireless network detectors. It is the most widely used open-source wireless monitoring tool.
Features:
- Open Source Wireless Monitoring Tool
- 802.11 Packet Sniffers
- Client/Server Model Architecture
- Runs on FreeBSD, Linux, NetBSD, OpenBSD and Macintosh OS.
Website: https://www.kismetwireless.net/
Pricing: It is open source free software that is distributed under the GNU General Public License.
7. Suricata

Suricata is an open-source network detection engine that is capable of inline intrusion prevention, offline processing, network security monitoring, and real-time intrusion detection.
Features:
- Open Source
- Lua Scripting
- Automatic detection of protocol
- Integrates easily with the network and can be embedded within numerous open-source and commercial solutions.
Website: https://suricata.io/
Pricing: It is freely available to use.
8. Security Onion
Security Onion is a free open source Linux-based distribution system that combines with other security tools and intrusion prevention systems within the custom-made Linux distribution. This tool includes such as Zeek, Snort, Suricata, and other open-source security tools.
Features:
- Network Security Monitoring
- Log Management
- Open Source Linux Distribution
- Integrates with multiple tools.
Website: https://securityonionsolutions.com/
Pricing: It is open-source IDS that is available free to use.
9. Sagan
Sagan is an open-source free Intrusion Prevention System that mines log files for event data. It can be run on various platforms like Linux, Macintosh OS, and UNIX.
Features:
- Open Source
- It is lightweight
- Compatible with Snort data
- Integrated with multiple third-party tools.
Website: https://quadrantsec.com/sagan_log_analysis_engine/
Pricing: It is open source so it is free to use.
10. McAfee Network Security Platform
McAfee Network Security Platform is not an open-source network intrusion detection system. It comes with very high pricing as compared to others with focused development, support access, and other benefits which are not available with other freeware open-source systems.
Features:
- Easy to use
- Network Traffic Inspection
- Network Analysis with extended Botnet Intrusion Detection.
- Advanced protection against threats.
Website: https://www.mcafee.com/enterprise/en-us/products/network-security-platform.html
Pricing: It is highly expensive that starts from $10,995.






